For my packet sniffing assignment, I ran Wireshark over a number of occasions to understand what kind of information was available to someone sitting on my network, who was talking to whom, etc. The collection instances are noted below:
- 30 minute period when I was web browsing
- ~7 minutes while I watched TV, and alternately played games on my Switch and browsed on my phone (I don’t usually try to do so many things as once, but thought it would be an interesting set of actions for this assignment.)
- A capture of a minute or two while I visited
https://www.nytimes.com,https://www.amazon.com, andhttp://neverssl.com/onlineusing the Tor Browser. - Same as above, but this time using Google Chrome.
I had exported each of these sessions as CSVs to analyze further using python-based tools, and also kept the capture session so that I could investigate particular packets more closely. I’ve reported some of topline highlights from each of these sessions below:
1. General Web Browsing
When I examined some of the most frequently appearing destinations, quite a few of the usual suspects showed up:
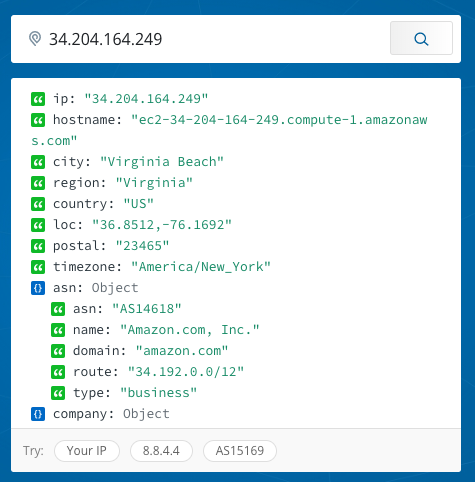
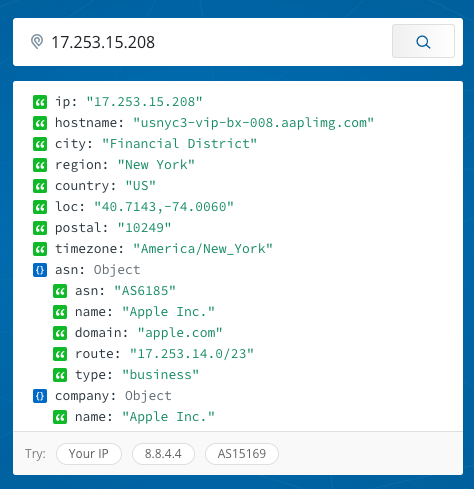
(I used IPInfo.io until I remember I could just resovle some of these addresses within Wireshark.)
An unexpected destination popped up in my packet sniffing:
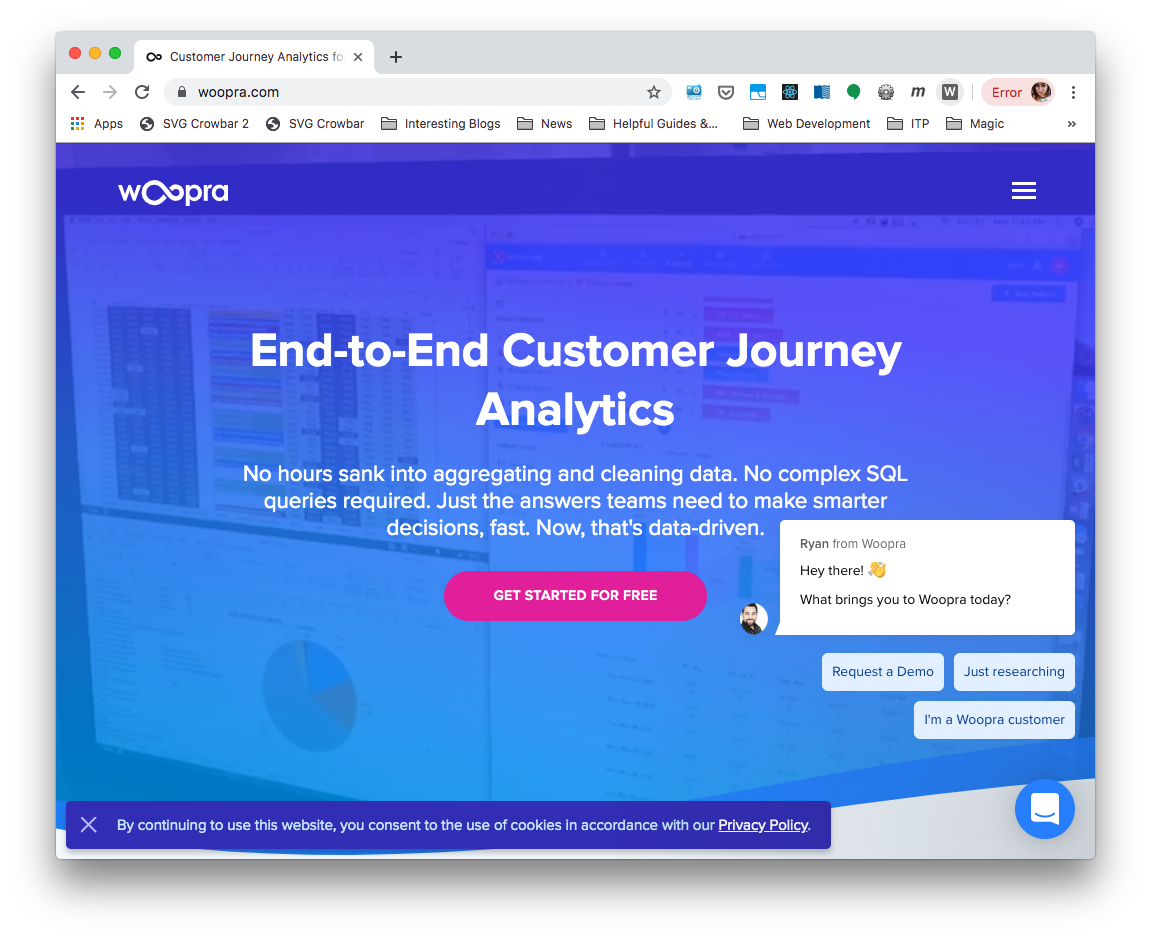
Woopra seems to be a service for collecting and analyzing customer journey analytics, and as you might suspect, this was not a website that I was visiting myself by going to woopra.com, but rather, what was visited on my behalf by some site or service I was using.
Another interesting tidbit that came out of my investigation of destinations was that the names of the slack teams I visited appeared in plaintext.

Besides looking at destinations, I also looked at what kinds of protocols were in use across my network:
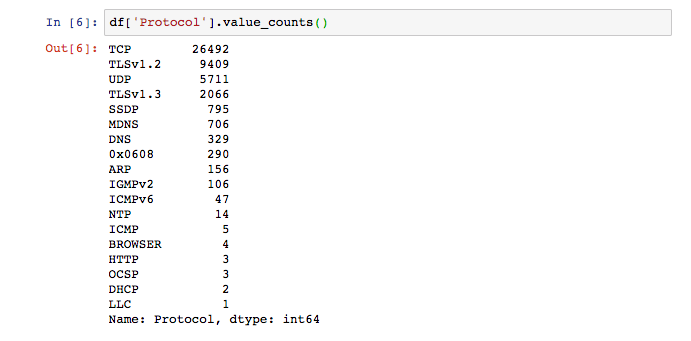
This particular protocol was unfamiliar to me:
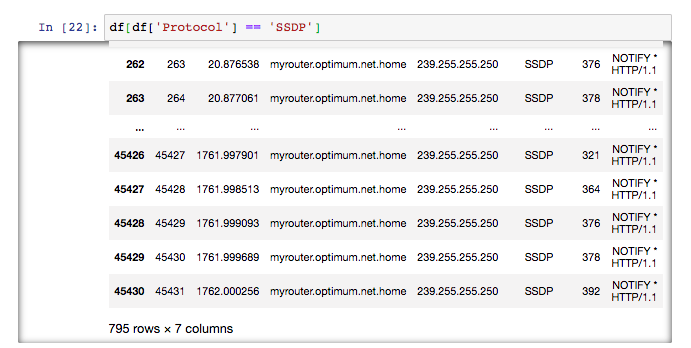
According to my research, SSDP stands for simple service discovery protocol, and can be used for advertisement and “presence” discovery, without the use of DHCP or DNS. The protocol uses UDP packets over port 1900, and devices use it to be easily discoverable to each other. Cloudflare, which had experienced a botnet attack over this protocol has a nice write-up about both the attack and SSDP.
In my case, it seemed that the source of my SSNP traffic was my router which was sending packets to 239.255.255.250. This conversation on DLS Reports seemed to suggest that my router was in multicast mode, and 239.255.255.250 is reserved by IANA for special purposes.
2. All the Entertainment Devices
This was a less exciting analysis than I had hoped. I was streaming from my Roku, and while you could see what I was using my Roku, you could not see what I was watching or even what video services I was using. Good for privacy, but less thrilling than Surya’s smart home adventures.
3. & 4. Browsing with and without Tor
Jackie and I attended a workshop about Tor by the Tech Learning Collective this weekend, and it inspired me to check out my packets while surfing the web on Tor. I only visited three new sites while packet sniffing: https://www.nytimes.com, https://www.amazon.com, and http://neverssl.com/online. I wanted to see if I could see that my traffic was in fact hidden when using Tor.
My browsing experience was immediately noticeably different when using Tor in the following way:
This was very visible in my Wireshark packet analysis. The most commonly appearing source was an IP address in Berlin:
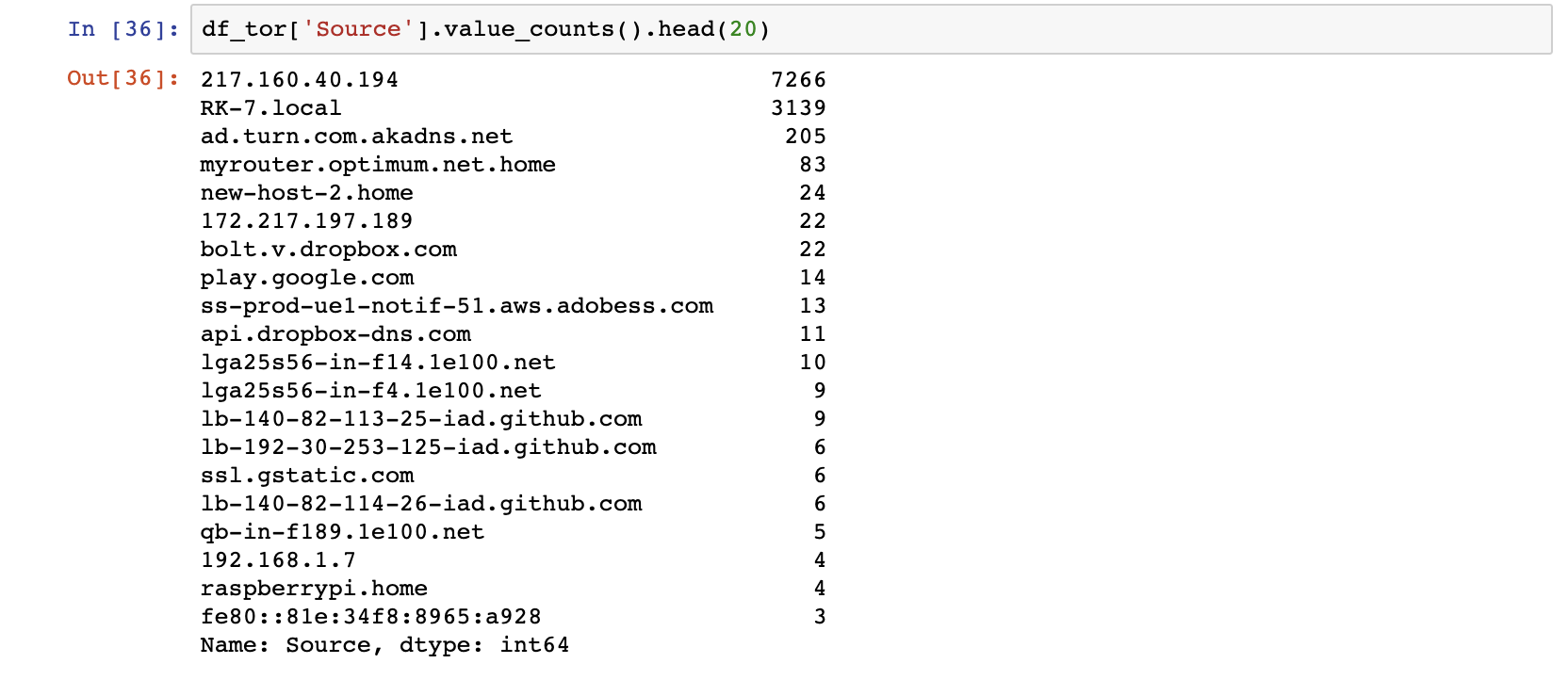
I did not take note of my Tor “circuit” at the time, but my guess is that this was my entry node into the Tor network. The prevalence of this IP address in my analysis reveals that ways in which your use of Tor would be visible to someone on your network or your ISP, but also that it does a fairly good job of hiding what websites I was visiting.
In comparison, my non-Tor-ified visits to the same websites were very visible in my packet analysis:
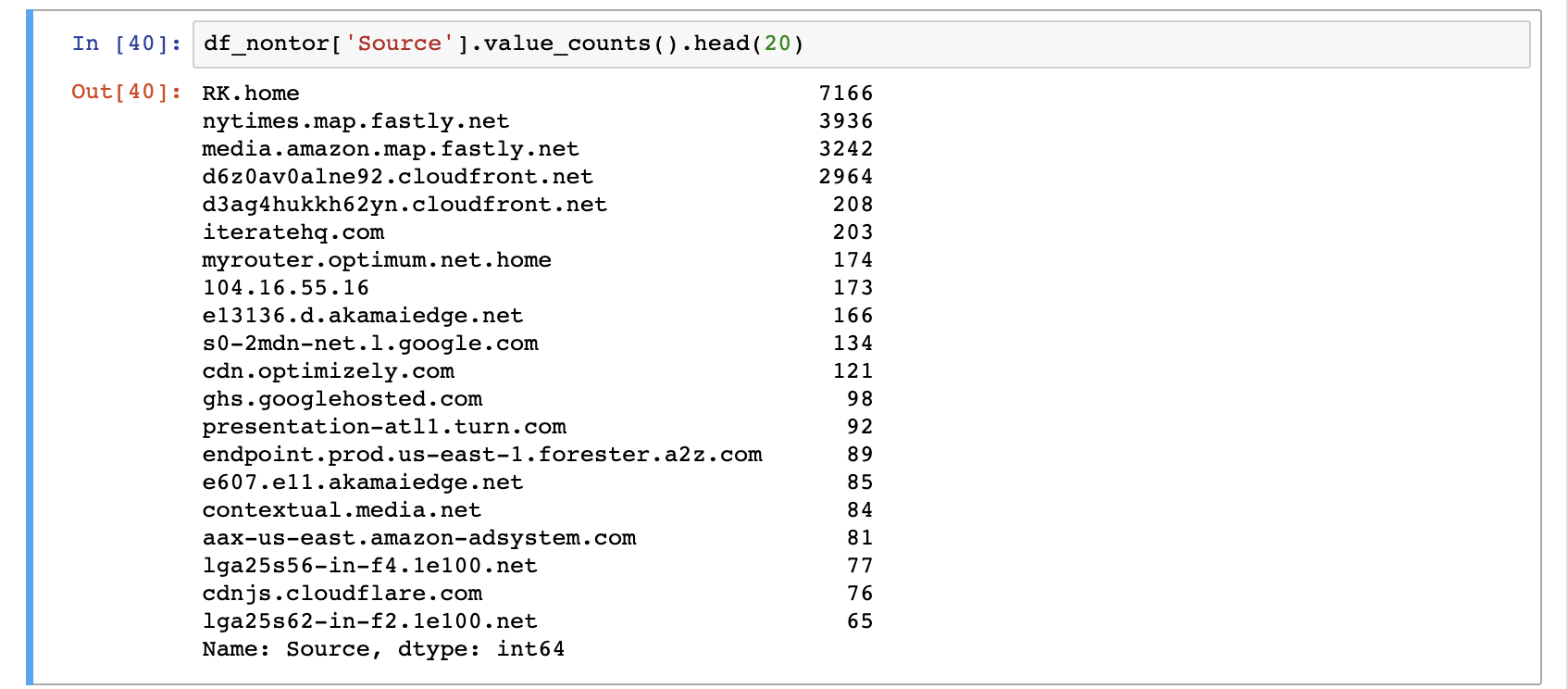
A quick look at my frames from this capture sessions reveals all the sites I visited.
Helpful actions in Wireshark
- Filter by keyword:
frame contains keyword(keyword should be some content you are interested in) - Analyze > Follow UDP/TCP/HTTP stream
Helpful Resources
