For this assignment, I added a firewall to my Digital Ocean droplet.
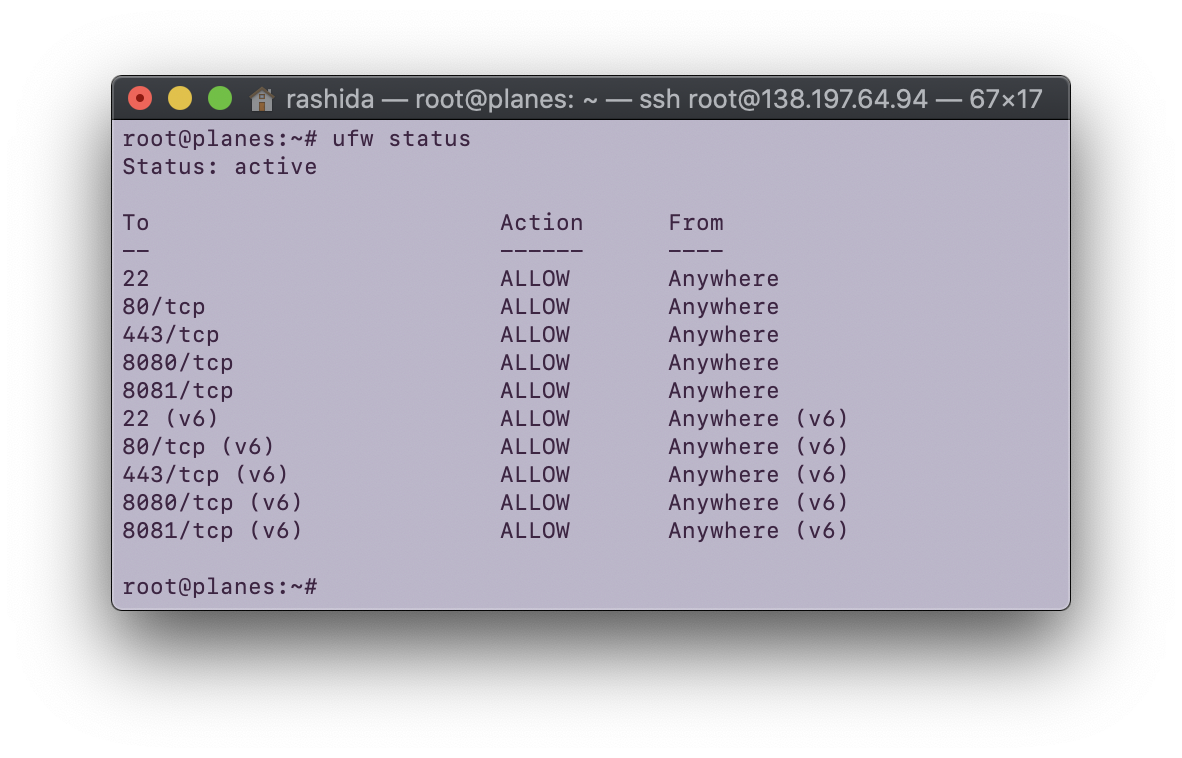
I analyzed my log results using python (code viewable below).
When I looked at the source IP addresses of the machines, the following locations came up:
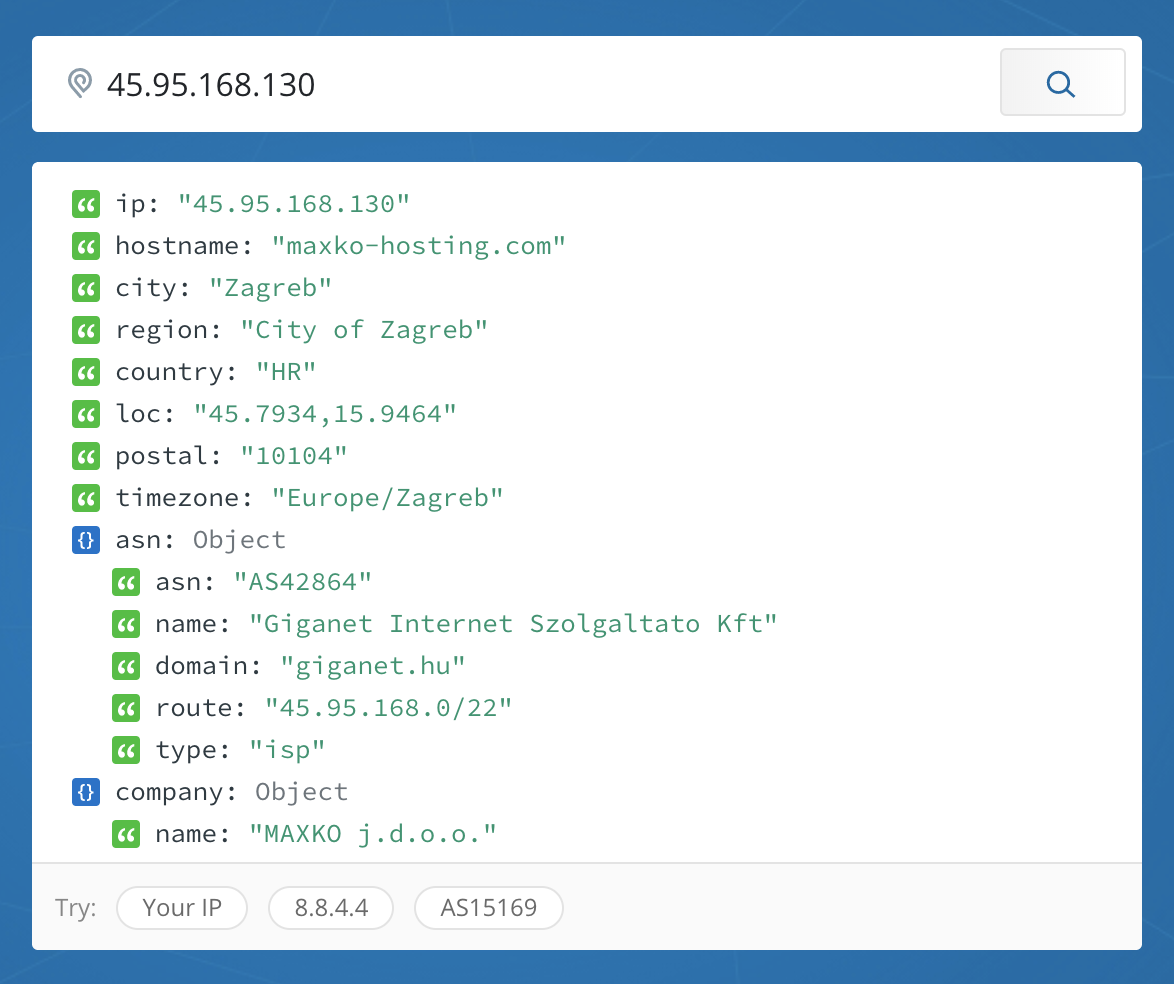
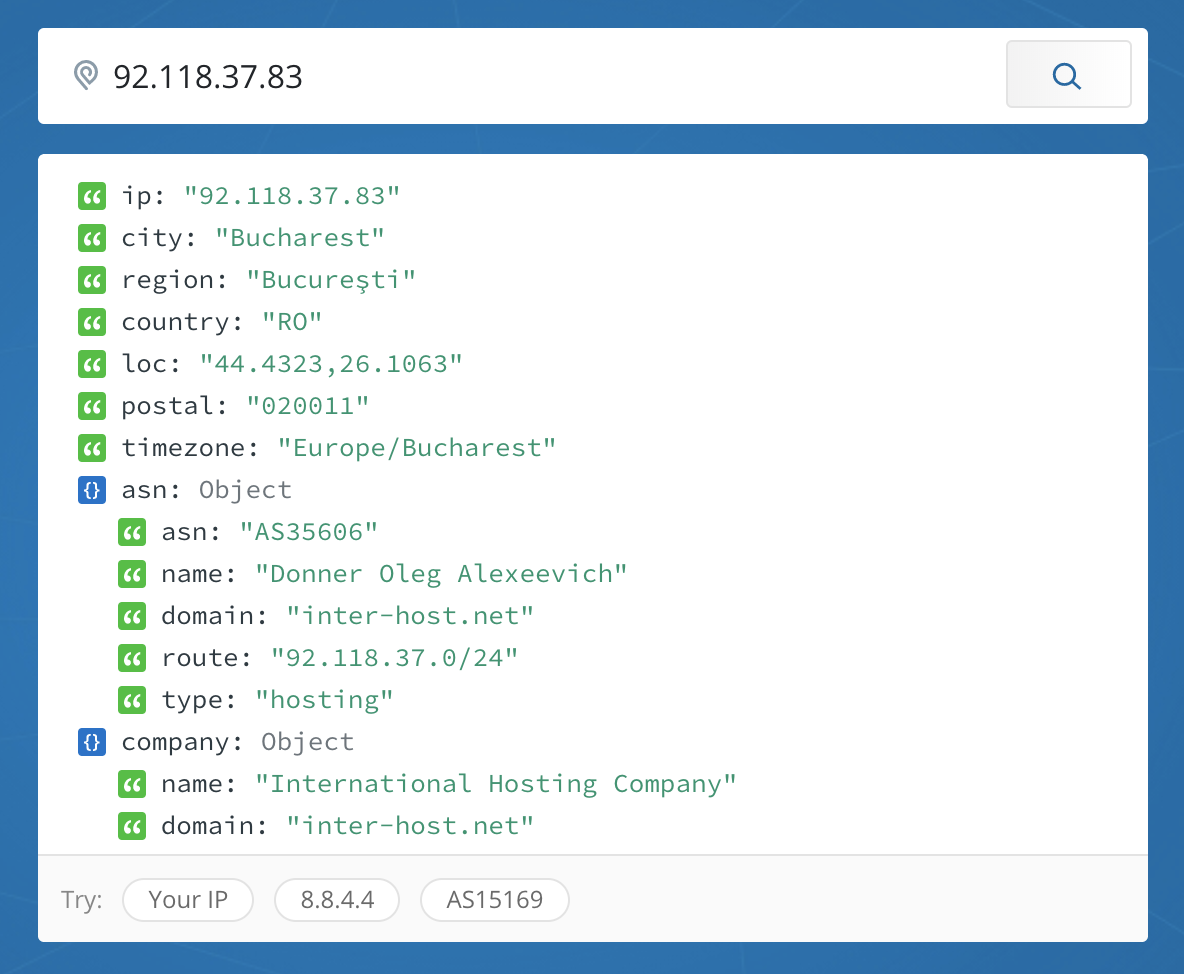
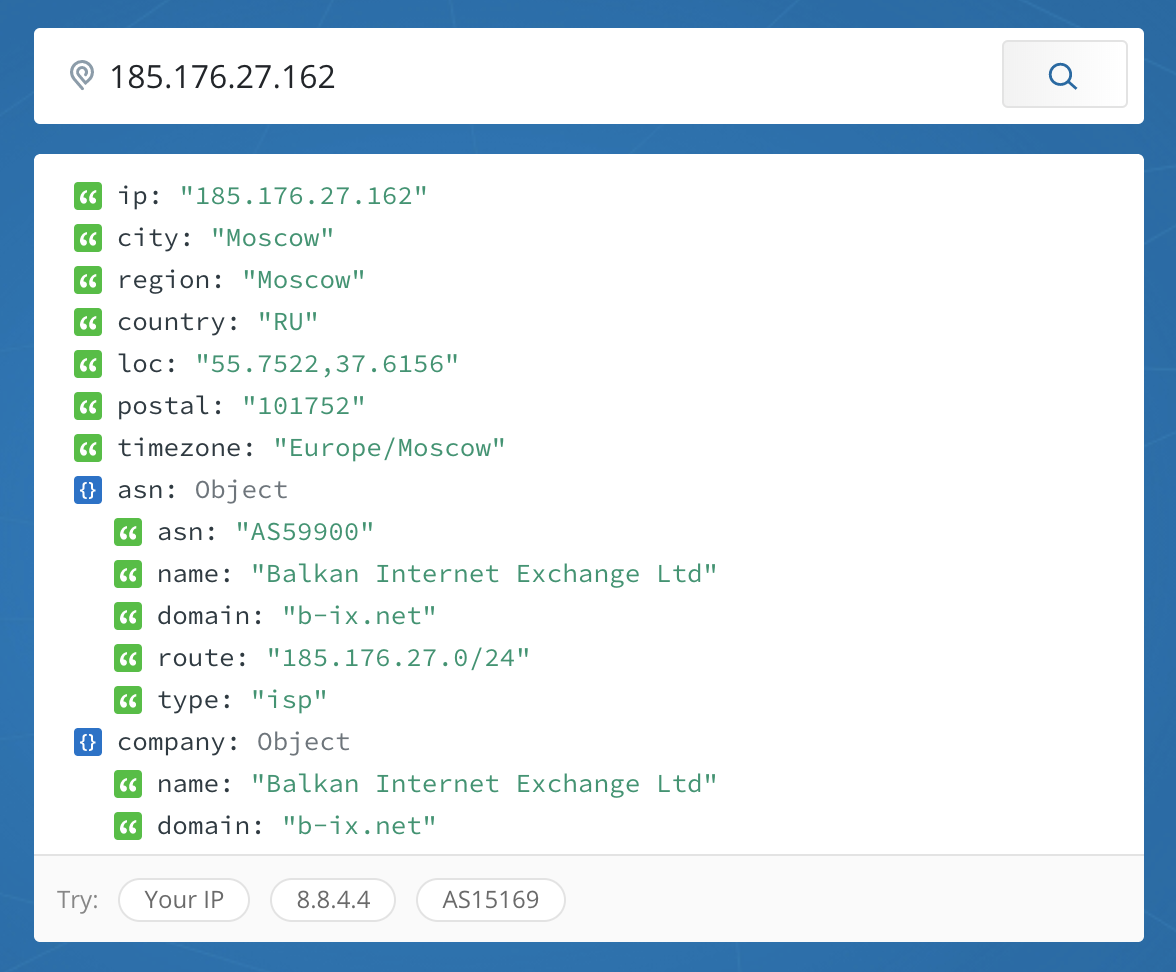
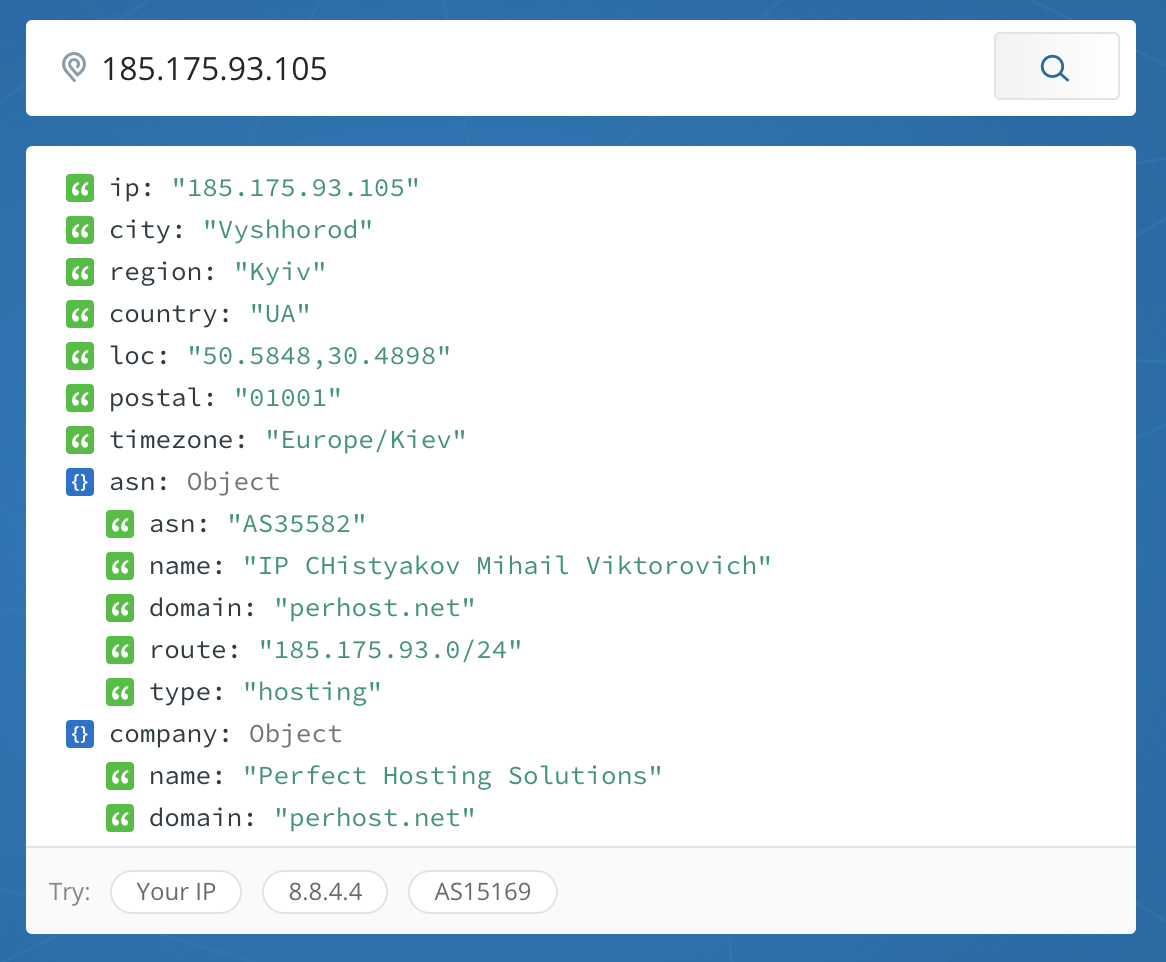
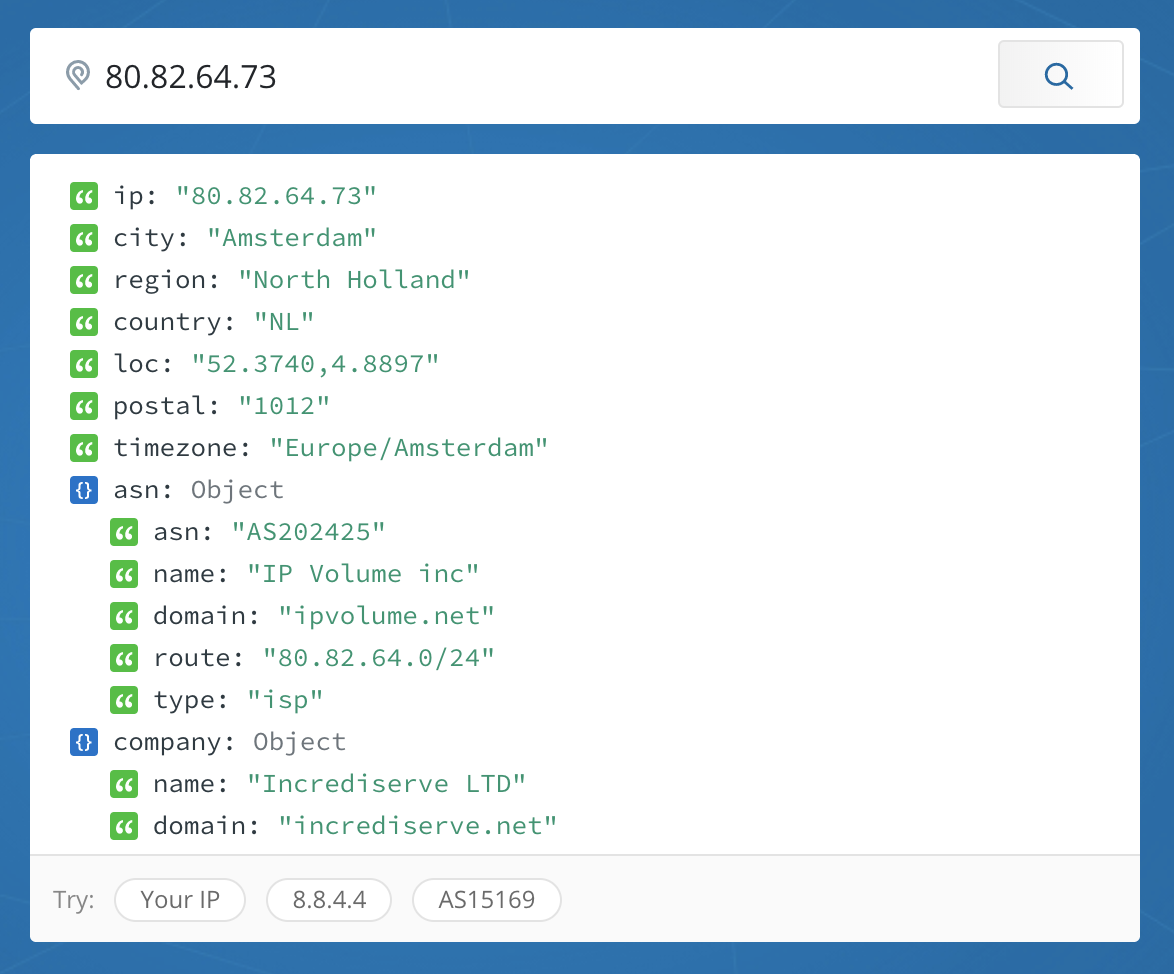
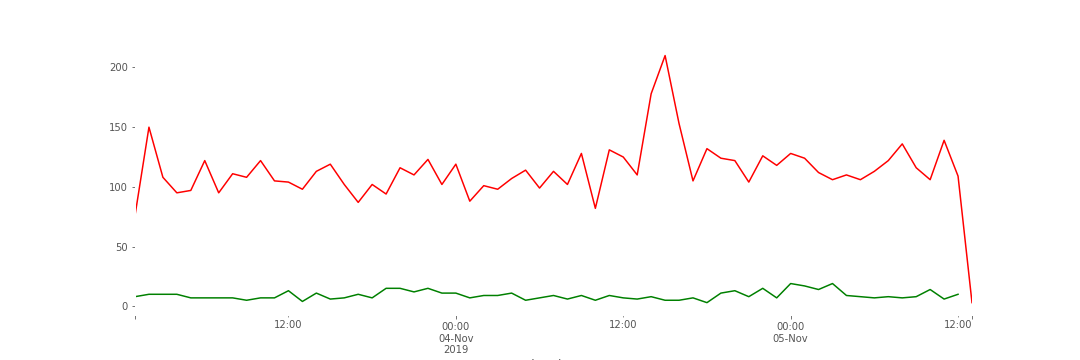
I also examined the results to see which protocols were most used. The following chart shows hourly hits, with TCP represented in red and UDP represented in green.
I also looked at which of my ports were being hit the most often. A few interesting ones:
- 1433: Typically associated with Microsoft SQL Servers. Known worms have used this port. (Source.)
- 60001: A few known trojans use this port. (Source.)
- 22: ssh!
- 3389 Sometimes used for Windows Remote Desktop services (Source.)
- 5060: A port usually used for VoIP or SIP (Session Initiation Protocol) (Source).
- 8545: The standard for for some Ethereum mining equipment. (Source)
- 6379: Post usually used for Redis servers. (Source).
